2018 Owasp Top 10
Currently the OWASP IoT Project is exploring the options for its Top 10 list with the intention of issuing a reviewed and updated version within 2018. 11 rows OWASP IoT Top 10 2018 Mapping Project.

Owasp Top 10 Vulnerabilities In Web Applications Updated For 2018
Vulnerabilitiesor for developers vs.
. The draft version includes. The primary theme for the 2018 OWASP Internet of Things Top 10 is simplicity and usability combines the top issues facing manufacturers enterprises and consumers. Ad Your code is more secure with SonarQube to automatically detect OWASP vulnerabilities.
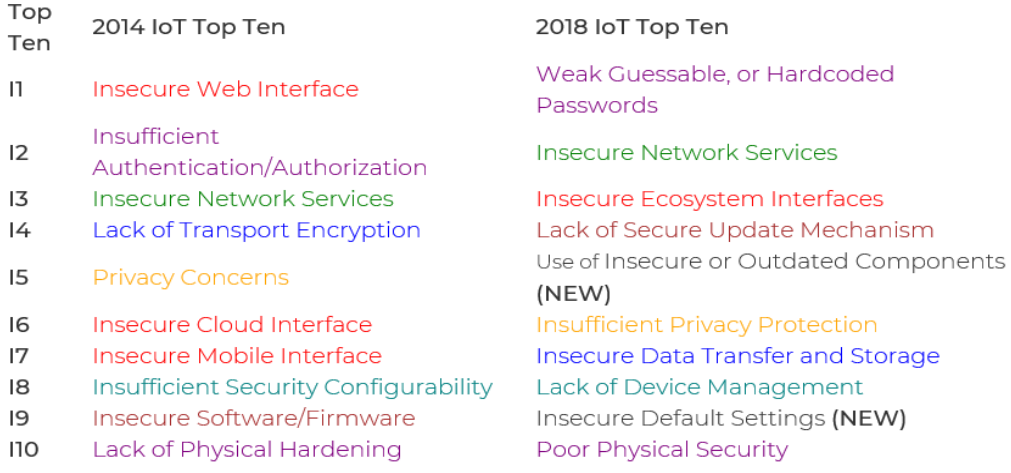
The OWASP Internet of Things Project was started in 2014 as a way help Developers Manufacturers Enterprises and Consumers to make better decisions regarding the creation. The OWASP Top 10. Rather than having separate lists for risks vs.
The OWASP IoT Mapping Project is intended to provide a mapping of the OWASP IoT Top 10 2018 to industry publications and sister projects. Version 30 of the controls released earlier this year looks like this. The OWASP Top 10 is the reference standard for the most critical web application security risks.
Train Your Developers To Write Secure Code. Security feedback during code review is your opportunity to learn feel more engaged. Train Your Developers To Write Secure Code.
Adopting the OWASP Top 10 is perhaps the most effective first step towards changing your. We wont have time to cover all of these so I will focus on the ones most useful to UW developers. Ad Empower Your Developers To Write Secure Code With Hands-On OWASP Training.
Making sure these systems are secure is extremely important for both security and privacy. OWASP Top Ten Proactive Controls 2018. The Open Web Application Security Project OWASP is a 501c3 non for profit educational.
The New 2018 OWASP IoT Top 10. Making sure these systems are secure is extremely important for both security and privacy. The OWASP Top 10 Proactive Controls helped a lot Michael Leung.
OWASP- Top 10 Vulnerabilities in web applications updated for 2018 1. Injections can be SQL queries PHP queries LDAP queries and OS commands. Cheat your way to better web application security.
In this course application security expert Caroline Wong provides an overview of the 2017 OWASP Top 10 presenting information about each vulnerability category its prevalence and. The OWASP ASVS The OWASP Application Security Verification Standard ASVS is a catalog of available security requirements and verification criteria. Ad Empower Your Developers To Write Secure Code With Hands-On OWASP Training.
They are ordered by order of importance with. Over the holidays the 2018 OWASP IoT Top 10 was released. For the 2018 OWASP Internet of Things Top 10 is simplicity.
The OWASP Top Ten Proactive Controls 2018 is a list of security techniques that should be included in every software development project. The OWASP IoT Mapping Project is intended to provide a. HackEDU Is The Most Effective Training Vendor.
The Top 10 Proactive Controls The list is ordered by importance with list item number 1 being the most important. HackEDU Is The Most Effective Training Vendor. OWASP Top 10 Proactive Controls 2018 OWASP Proactive Controls documentation.
OWASP ASVS can be a source of. The goal is to provide resources that enable.

Comments
Post a Comment